When you are on the road, your phone suddenly receives a text message from a strange mobile phone:
Hello brother, I have a difficult family sister, my mother is sick. She wanted to use her first time for the mother's medical expenses, hoping that a good-hearted brother could help her.
You just walked out of the Agricultural Bank of China. The phone received a message from 95599:
Our bank will deduct 1920 yuan from your account today. If you have any questions, please contact: 400XXXXXXX Agricultural Bank of China.
You sit at home and your mobile phone receives a text message from 95588:
Dear ICBC user: Your mobile bank has already fulfilled the cash gift package of RMB 4690. Please log in at http://9558onz.com to collect it.
This information or temptation, or consternation. However, their role is only one: to accelerate your heartbeat through a string of text, and then take the initiative to follow the message prompts and get in touch with each other.

Pseudo base station burst fraud messages/images provided by Baidu X-Team
Yes, one by one, a lively scam, is at the other end of the line, with a bloody opening.
Truthfully speaking, the swindler's polishing of the scam script has reached the level of “Huayi Brothers.†Not only is the plot dripping, but there are also professional actors who use “public, prosecution, and lawâ€. Perhaps the liar also believes that "good start is half of success", so the first step in the scam "send text messages" has done enough homework.
A “professional†who “pursues†has the following two characteristics:
1, can forge any signal code, so that the deceived convinced.
2. Fraud messages can be issued on a large scale to ensure that the base of “prey†is large enough.
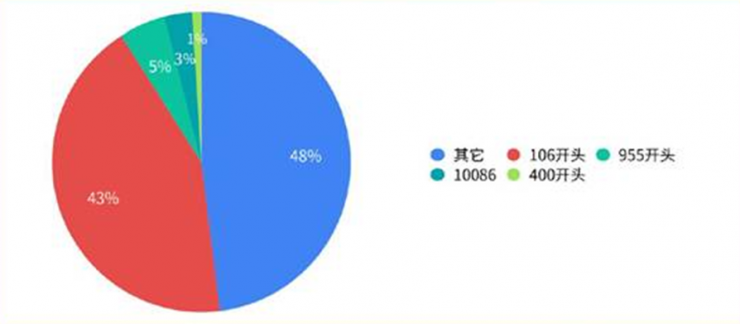
Pseudo base station disguise the proportion of various numbers
Pseudo base stations are an excellent choice for them. These devices are often placed in the trunk of the car, or even in people's backpacks, and send these “scam entrances†to nearby mobile phones—scam messages.
For world peace, police uncles are tracking these pseudo base stations every day. However, the "automobile party" and "backpacker" of the pseudo-base station do not seem to have a big difference in appearance. How to get a liar in the vast sea of ​​people is actually a tricky issue. To this end, grassroots police uncles will use an artifact—pseudo-base station monitoring and warning platform—that can track and locate these pseudo-base stations. The Leifeng network resident channel (WeChat ID: letshome) interviewed the developer team of this artifact. Huang Zheng, head of X-Team, Baidu Safety Labs, listened to him and told him how to use technology to "kill" pseudo-base stations.

Pseudo base station in car trunk
Pseudo base station madness As an anti-black expert on “professional fight against black production for 20 years,†Huang Zheng has studied almost all the loops of interest behind these messages. He divided these "pseudo base station information" into three categories:
1. Camouflage bank or telecommunication operator official customer service , send fraudulent information of point exchange or banking business, trick users into the URL specified by the fraudster, these URLs may be a Trojan download link, once downloaded, can intercept the password information in the mobile phone; It may be a fake official website that tricks users into entering personal information and password information.
The content of these fraudulent messages is highly related to the signal code, and the website is similar to the official one, and it is easy to induce people to be fooled.
2. Pseudo base stations will also be heavily used to send advertisement information , such as real estate opening, gambling, and pornographic information.
3, pseudo base stations will also be used by criminals to take a walk rumor .

Pseudo base station fraud "standard process" / picture courtesy of Baidu Security X-Team
Huang Zheng said that high-power pseudo-base stations can radiate the range of 2 kilometers around, and backpack pseudo-base stations can also reach the range of several hundred meters. The nature of this “near people†has spawned many geographically relevant “application scenariosâ€. E.g:
1. The fraudster may assume a pseudo-base station near the bank and specifically send the bank's fraud message to the person who runs the bank's business. For example, people who have just completed business at the Agricultural Bank will receive more information from the Agricultural Bank of China and will be more vigilant.
2. Criminals may use pornographic base stations to distribute pornographic advertisements for “special services†around the hotel and send them “intimate serviceâ€.
3. Some people even distributed rumors specifically against commercial competitors, such as the following wonderful text message:
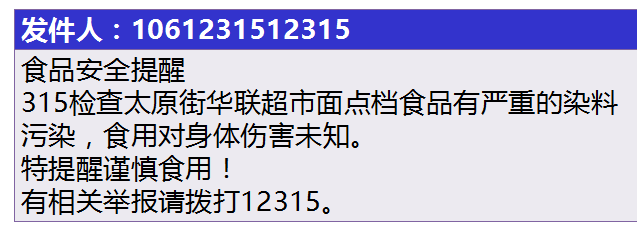
Obviously a malicious base station maliciously destroyed by competitors
At present, pseudo-base stations are most widely used to send spam messages, but if you think that pseudo-base stations can only be used to send spam messages, then “Tusen is brokenâ€, and Huang Zheng tells Lei Feng to visit the channel. Public ID: lets home): As the name implies, the pseudo base station is a forged communication base station, so it is theoretically possible to disguise the functions of all normal base stations. He told us about the terrible power of pseudo-base stations.
Advanced deception 1: You call the bank's official customer service, but it is a liar.
If your mobile phone is connected to a pseudo base station, it means that the mobile phone believes that it is a real existing base station that interacts with him.
Here is a simple science popularization: There is a unique IMSI number in the SIM card of the mobile phone. The operator assigns a mobile phone number to the card according to the IMSI number. Similarly, the phone number dialed by the mobile phone also corresponds to an IMSI number. And this number can be defined by the base station.
In this case, if your cell phone is connected to a pseudo base station, then whoever dials your phone at this time is the one designated by the fraudster. For example, if the fraudster defines 95588 in the base station, the number is directed to his own phone. Even if you do not click the fraud link in the fraudster's text message but call the customer service phone to confirm, still do not relax your vigilance. It is likely that you trust. Customer service is still a liar on the phone.

Red is a counterfeit phone for a pseudo base station, and there is no difference between an official phone and an official phone.
Advanced fraud, you enter the official website, you may also open the phishing website
Huang Zheng continued to imagine a terrible scene for the Lei Feng network resident channel (Weixin public ID: letshome). The current pseudo-base station equipment on the market can only provide 2G networks, but it can intercept all your network traffic and can “hijack†addresses.
For example, in the scope of the pseudo base station, you received a text message from the "bank", you want to check the official website to find out if your balance has changed, but even if you entered the official ICBC website accurately, The fraudster next to the base station can also return to you a fake version of the ICBC website through simple settings.
Due to the personal input of the web site, the victim of self-confidence is likely to be completely immersed in the scam and thus suffer serial scams.

An ICBC phishing website is difficult for ordinary users to identify
Under the pseudo-base station network, don't think that it is safe for you not to log in to the bank's related websites. In fact, fraudsters can still intercept your WeChat friends' photos, microblog images, and so on. Using this information, swindlers can obtain personal privacy, living environment and many other personal privacy, and thus continue to defraud in a targeted manner. And if you landed on a website in a pseudo-base station network environment, hackers could immediately obtain your login cookie and immediately log in on another computer.
At present, there are very few fraudsters who choose to use “pseudo-base station calls†and “network hijacking†to defraud. The reason is not that these “high-level†technologies are so complicated that they are difficult to master, but because they use the basic fool scam Enough to get a good income. However, these possibilities demonstrated by Huang Zheng for us are enough to show that there are many possibilities for scams. No one can rely on their IQ to stay away.
Pseudo base station "underground party"
If you have a working day salary of 5,000, will you be tempted?
Huang Zheng, who has conducted an in-depth investigation of the pseudo-base station ecology, told Lei Feng Network Channel (WeChat ID: letshome):
Those who install pseudo-base station equipment in the trunk, as long as they complete the daily tasks, such as sending hundreds of thousands of text messages, may receive about 5,000 yuan in remuneration.
Although high-power signal amplifiers can cause harm to the human body, some people still take risks for such income.

Device used to make a pseudo base station, BladeRF (about $500, coverage band 300M-3.8G)
Here, it is necessary to popularize the working principle of the pseudo base station:
The existence of a pseudo base station comes from spells of the last century. Just mentioned, the pseudo base station can only provide 2G service. This is actually related to her working principle.
At present, 3G and 4G networks, which are now widely used, adopt a two-way authentication model. In simple terms, while the base station verifies the legality of the mobile phone, the mobile phone also verifies the legitimacy of the base station.
However, the commercial 2G network protocols that began in the 1990s are subject to technology and security awareness. They only provide verification of the base station to the mobile phone, and the mobile phone has no right to verify the legitimacy of the base station.
This communication protocol from the last century is the soil where pseudo-base stations can survive. Since the popularity and availability of 3G GSM networks in China (again in many other countries) are abnormally high, in the absence of 3G and 4G signals, the handset will drop to 2G signals by default. In this band, the handset will only connect. The base station with the strongest signal, it can be said that the world of 2G is a paradise for pseudo-base stations.
Therefore, a complete pseudo base station, including a high-power signal suppression device, plays high-intensity noise in the 3G and 4G bands, and then forces the handset to connect to the disguised 2G signal. This is also the reason that the base station has harmed human health.

Pseudo base station installed in the trunk of an electric vehicle
Slow travel, emergency self-destruction - pseudo-base station black technology
Huang Zheng told Lei Feng network channel guest channel (WeChat ID ID: letshome), the initial pseudo-base station was only placed in the car, and then parked in the "proper location" for one day, but as the police crackdown, the current The “automobile party†is driving a car (or electric car) and pulling a pseudo base station to “slow travel†on a fixed route in a bustling area. There are also some "backpackers" who shuttle back and forth between pseudo-base stations in crowded places.
However, it is obvious that these "automobile parties" and "backpackers" are all so-called "horses" and they have never even met on their own. Huang Zheng said:
General tasks are issued online and even the equipment used by the pseudo-base station is sent to the "horse" by mail. Many of these devices are from Huawei and other large companies. They were originally used to set up communications networks in areas with poor terrain and complex networks. The information sent is also stipulated by the on-line. Therefore, when the police strikes, it is often difficult for the black-industry gangs to be willing. It's not because Ma Zi didn't say "say death," but they didn't know it at all.
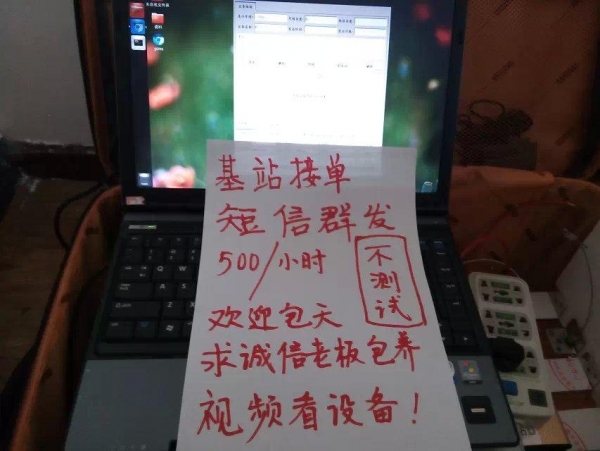
Pseudo base station orders
In addition, by studying equipment distributed by pseudo-base station gangs, Huang Zheng also found that the more advanced pseudo-base stations actually joined the "self-destruction function."
The so-called self-destruction function means that only a single key press is required to clear the short message sending record on the pseudo base station. This function is directly integrated into the "finished product" of the pseudo base station.
Why is there such a function? He said the reason:
This is because relevant laws stipulate that if more than 5,000 spam messages are sent, they can be sentenced. However, if only 100 were sent, the maximum amount of “crimes against national communications†would be pursued , so that severe punishment would not be achieved and criminals would be able to escape impunity. This is one of the reasons why pseudo-base station backpackers continue to ban.
Children's shoes may be concerned about whether or not there are pseudo-base stations near where I live.
Huang Zheng showed a set of data for Lei Fengwang (searching for "Lei Feng Net" public concern) :
Taking Beijing, where Baidu’s headquarters is located, as an example, pseudo-base stations are active in the areas along the Metro Line 10 from Panjiayuan to Tuanjiehu, Beijing West Railway Station, Beijing North Railway Station, 798, and Sanyuan Bridge. The number is about 900. In just one month, the pseudo-base station detection platform intercepted 30,000 text messages.
In fact, Beijing is also the most rampant area for all Chinese pseudo-base stations. The children's shoes of the Royal Capital need to be careful.
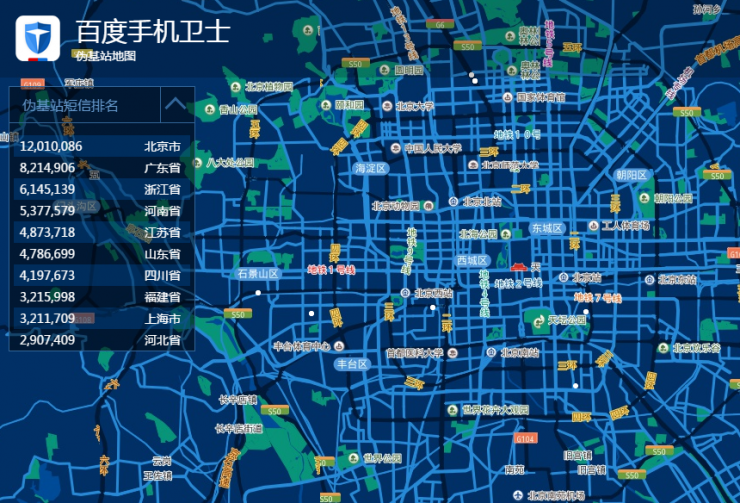
Pseudo base stations SMS rankings/images by provinces and cities provided by Baidu Security X-Team
How to "kill" pseudo base stationsHow do you know that a mobile phone has entered a pseudo base station?
Here also needs a simple science:
Each base station contains four sets of digital "identity information". The first two groups define the operator's network. The latter two groups define the location of the base station. The location information of each base station can be found based on these four groups of numbers.
Huang Zheng said that the current pseudo-base station does not have such a high level of intelligence. It is just a “fool†device. It will not accurately simulate the ID of the real base station, and the last two positions are often random.
As a result, there are the following methods:
If you monitor the cell phone's base station parameters, the last second is still in Haidian, Beijing, and in the next second it will be in Guangzhou. It is very likely that the cell phone has been “captured†by the pseudo base station.
Use the GPS, Wi-Fi and other signals on the mobile phone to check the location of the base station. If the base station's ID information shows that it should be in Beijing, but the positioning of the mobile phone is clearly in Xi'an, it is very likely that the base station is an illegal "knock-off cargo."
Huang Zheng said that according to the signal strength of the mobile phone, the distance between the mobile phone and the base station can be roughly determined, and based on the positioning information of the mobile phone, the location of the pseudo base station can be judged. The accuracy of this position is about 100-500 meters. If the mobile phone is not connected to Wi-Fi, or if GPRS traffic is not turned on, or the surrounding buildings are too complex, it will affect the determination of the distance to the pseudo base station.

Pseudo base station SMS notifications and positioning/pictures provided by Baidu Security X-Team
However, this technology has a very important role, that is, the pseudo-base station has just begun to run, about 10 minutes to the police warning platform to issue an alarm, and give the location. Without actually being victimized, it was reported to the police station that the police realized that someone had set up a pseudo-base station.
Huang Zheng said that the detection function of this pseudo base station is currently integrated in Baidu Mobile Guardian, and Baidu Maps may also join this interface in the future.
Once it is detected that the mobile phone is in a pseudo-base station, it can be basically determined that the content of the message is illegal or fraudulent information. Combined with the analysis of the artificial intelligence and big data, malicious phishing websites and means for fraud can be extracted. The pseudo-base station messages mentioned at the beginning of the article are intercepted in this way. Huang Zheng said that after extracting these phishing websites, Baidu will also ban the illegal websites on its own platform and cooperate with police uncles to do the tracing work of the gangs behind the website.
Huang Zheng still feels proud of his team’s technology. “Over the past year or so, our platform has covered public security in all provinces and cities except Xinjiang and Hong Kong, Macao and Taiwan, and we have uncovered more than 800 false base station fraud cases,†he said.
Objectively speaking, the police are also struggling with counterfeit base stations. For example, criminal gangs of telecommunications fraud are often on the other side of China, and servers on phishing websites may use foreign servers as springboards. All of these will make the cost of handling cases increase rapidly.
However, when you know that a technology like Huang Zheng is using his top technology to help police uncles and pseudo-base stations die, perhaps you will see some hope.

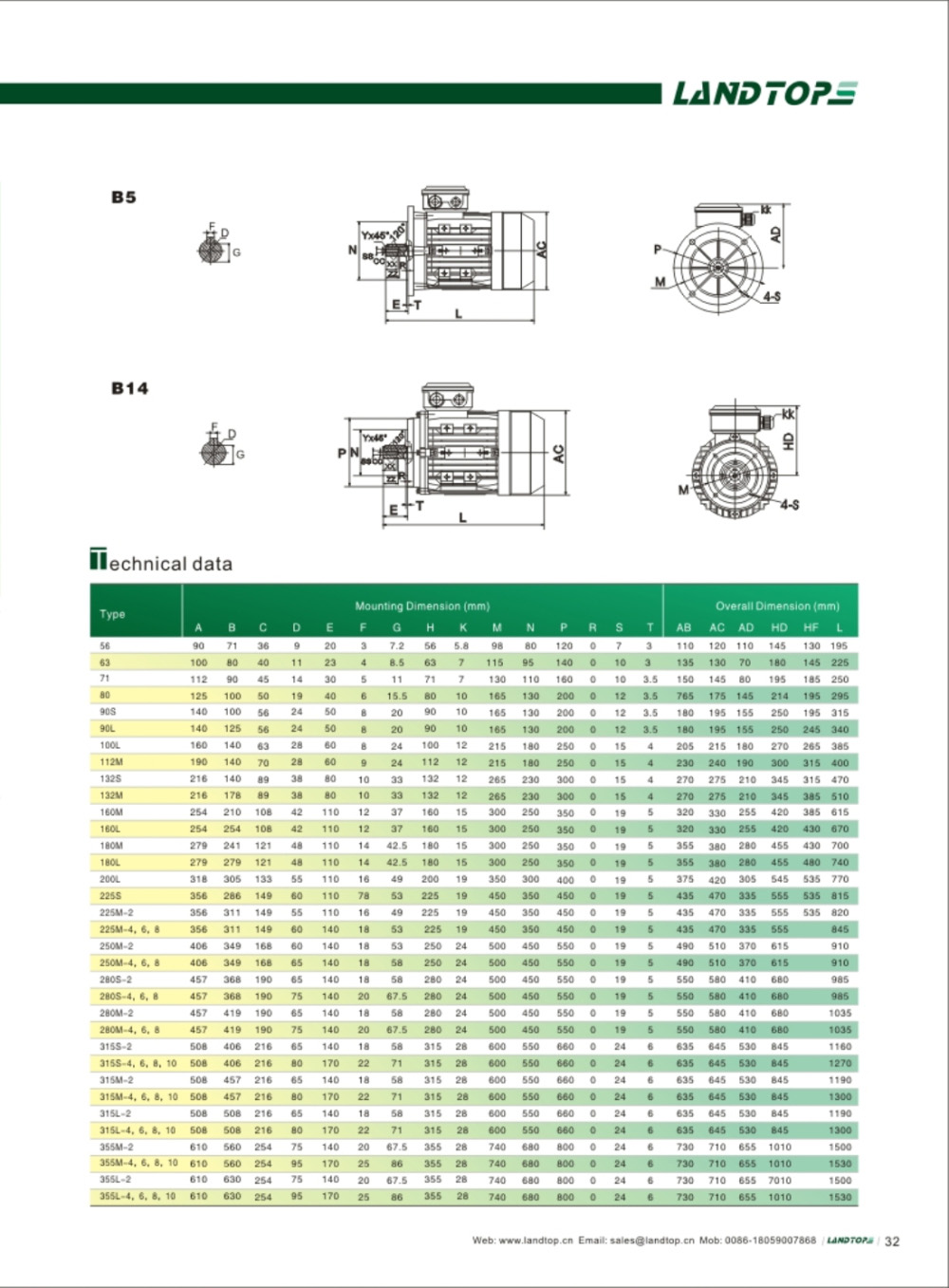
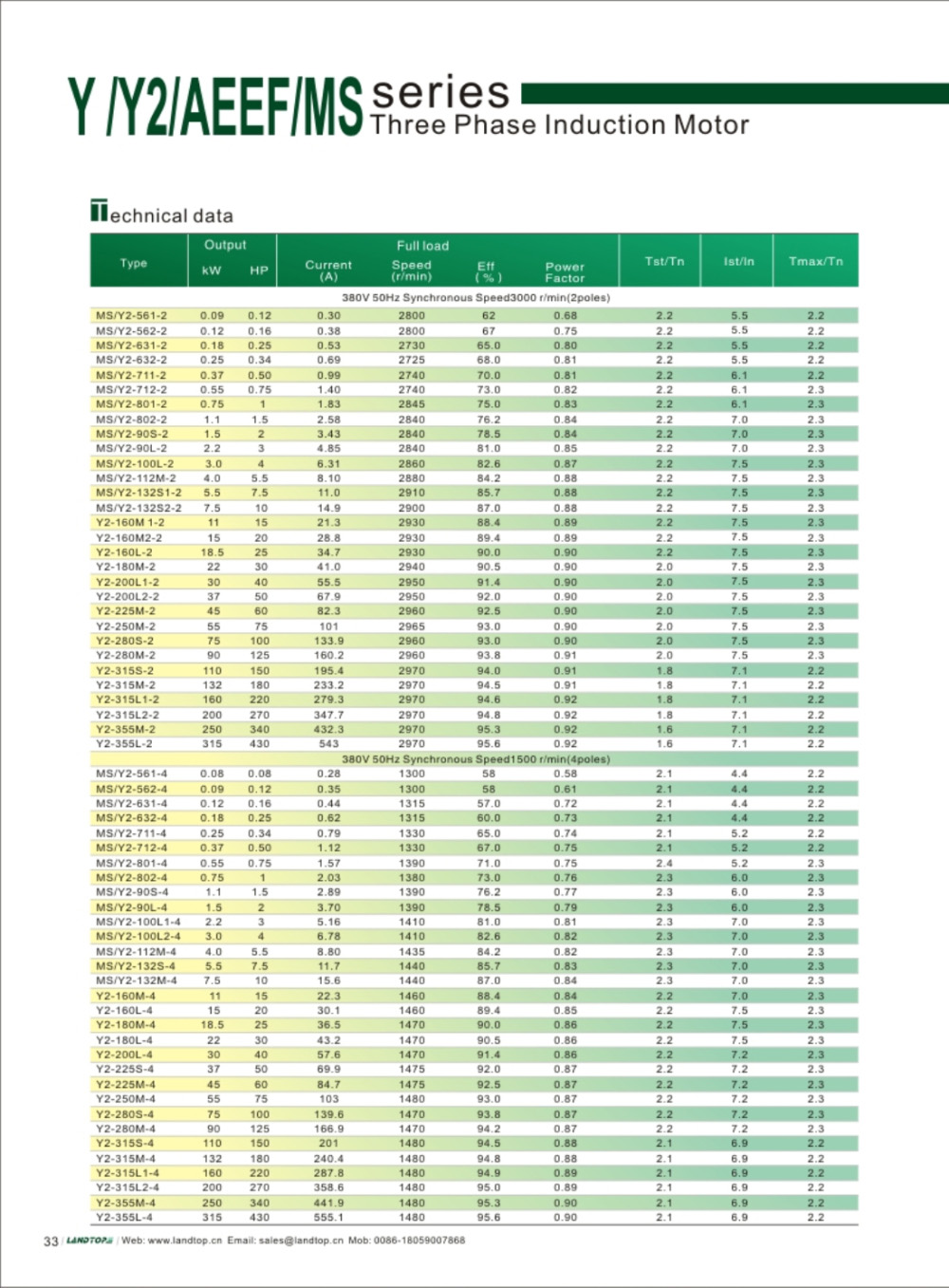
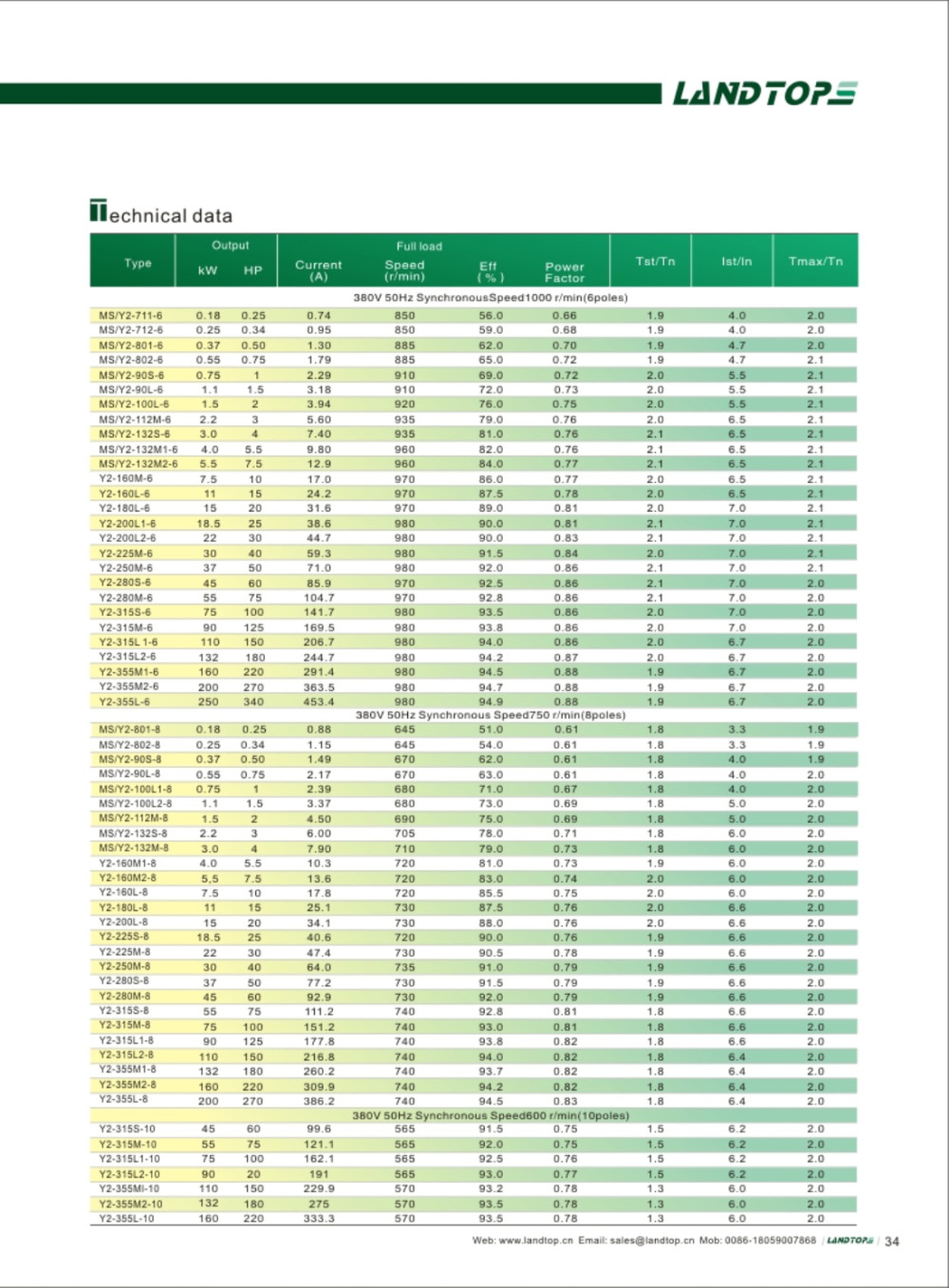
Y2 Three-Phase Iron Housing Electric Motor
Y2 Series 3-phase Cast Iron Housing Induction Motor
Y2 series motor is totally enclosed and fan cooled 3 phase squirrel cage induction motor. It is newly designed in conformity with the relevant rules of IEC&DIN42673 standards. Y connection for motor of 3kw and below. Delta connection for 4kw and above.
Application:
Y2 serise 3 phase motors are widely used as driving equipments of various machineries such as: machine tools, blowers, pumps, compressors, transporters, agricultural and food processing.
Operating Condition:
Altitude ≤1000m
Ambient temperature -15°c to 40 °cRated voltage 380V, 400V, 415V, 220V, 230V, 240V, etc
Rated frequency 50HZ, 60HZ, 50HZ/60HZ
Insulation class Class B, Class F
Duty Continuous(S1)Protection class IP44, IP54, IP55
Cooling method IC0141
Note:
The voltage and frequency could be made according to your request. If there is any requirements or inquiries, welcome to contact us.

Y2 Series Three Phase Induction Motor,3 Phase Electric Motor,3 Phase AC Motor,3 Phase AC Induction Motor
FUZHOU LANDTOP CO., LTD , https://www.landtopco.com