Discussion on Authentication Method of Network System Security Access
Network equipment such as Ethernet (intranet, Internet), wireless communication network (cellular phone, WiFi) and power line communication (PLC) are composed of servers or base stations and network nodes or network equipment. Mass-produced network equipment is based on specific networks Capacity to assemble. In order to obtain a controlled and highly reliable network system, developers face two major design challenges: all devices connected to the network must be certified; remote upgrades through the server are allowed.
It is very difficult to authorize and authenticate the devices connected to the network. Unauthorized equipment may directly damage the supplier's revenue by disrupting system performance and disrupting users. However, the network authentication function also provides suppliers with a second business opportunity, that is, the user device that purchases the upgrade function is upgraded through the server.
Comparison of several major network authentication methods
The authentication process is the process of establishing an identity between two targets (referred to here as servers and network devices). The certification process must avoid counterfeiting or simulation activities by unauthorized manufacturers or clones. The best way for identity authentication is to use a system token, and the network device processor communicates with the authentication token to authenticate the device. Appropriate configuration of authentication tokens restricts the access of devices, and ultimately eliminates the access of fake and inferior network devices.
The server of the local network is close to the network equipment, and it is difficult to upgrade through the manufacturer. For example, a printer with accessory modules (such as ink cartridges), where the server is the microprocessor in the printer and the network devices are those modules.
The working environment of the server on the remote network is safe, but the service provider maintains access rights to it. The remote network has some potential problems such as unsecured communication links, but it does provide convenience for practical applications: according to the judgment of the central server, it can be expanded and detected after the network installation is completed (Figure 1) .
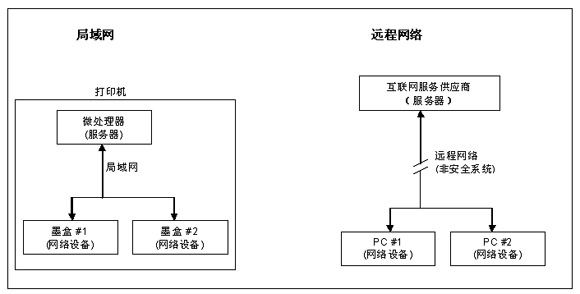
Figure 1: After the device is delivered to the user, the network operator usually does not have the right to access the local area network (left side); the remote network (right side) has access rights even after the user is delivered to the user.
Studying the working environment of the remote server carefully and comparing the cost and advantages of several kinds of access control can make you apply the best authentication method in the specific system. Authentication schemes include: simple password authentication, symmetric key authentication, public key authentication, hash authentication, etc. The following also discusses the advantages of the network device upgrade function.
Simple password authentication The simplest authentication method is to determine whether the password is correct. This method has the lowest cost because no additional hardware or software is required to support the encryption / authentication algorithm. Since the password is transparently transmitted, that is, transmitted through the communication link, it is easy to be intercepted and copied later (Figure 2). It can be seen that the security of the simple password verification scheme is poor.
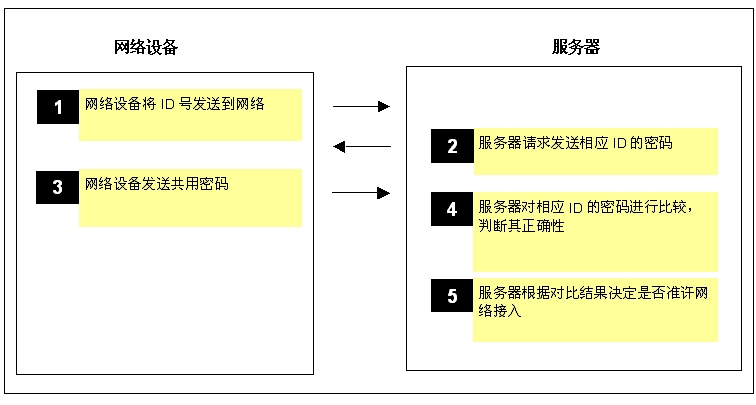
Figure 2: The third step of the password verification communication is likely to cause the key to be stolen
For basic password authentication, the network device and the server must have a recognized key. If the network device has a unique identification code, the identification code can be used to form a unique key for the device.
Symmetric key authentication uses an encryption algorithm to send security information from a network device to a server. The security device needs to program the encryption key into the network device. There are two types of encryption keys in practical applications: symmetric keys and asymmetric keys (public key / private key). The symmetric key shares the same key on the server and network equipment (Figure 3).
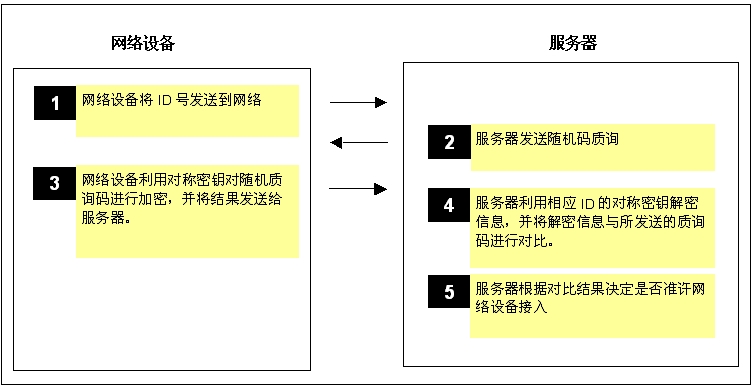
Figure 3: In symmetric key authentication, random challenges can avoid repeated response communications
Using a processor to achieve this authentication is relatively simple, but more cumbersome than simple password verification. Since the communication data between the server and the network device is encrypted and cannot be emulated by an attacker, this method has high security. On the other hand, symmetric encryption algorithms usually only use simple operations, such as "or" operations and shifts. The specific implementation cost is not high, which can be realized by using a microprocessor.
The premise of this solution is that the network device and the server must have a common symmetric encryption key. If the network device has a unique identification code, the identification code can be used to form the unique key of the device.
Asymmetric key authentication Asymmetric encryption systems (public key / private key) do not share the same key, and each device contains a private key and a public key. Certificates can be installed on network devices to verify their authorization. Since the public key / private key algorithm involves a lot of calculations, the implementation scheme requires a large storage space and CPU resources, and the cost is high (Figure 4). For example, RSA public key encryption requires modular exponentiation. In addition, it should also be noted that devices using this type of encryption algorithm are subject to US government export restrictions.
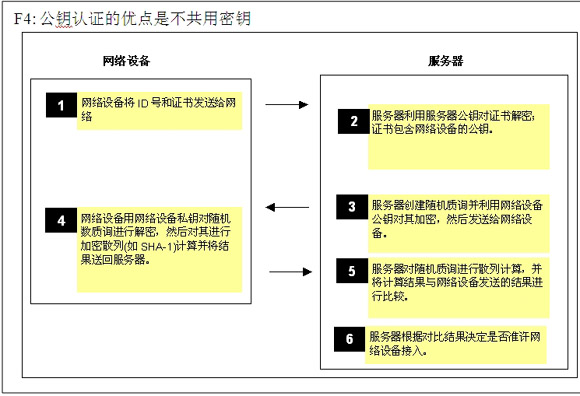
The premise of this solution is that the network device must be loaded with a certificate containing the network device's public key and encrypted with the server's private key. After decrypting with the server public key, you can verify the legality of the network device.
The authentication hash (Hash) algorithm based on the hash algorithm is to convert a string of characters into a shorter, fixed-length numeric value or encrypted information to represent the original string. Hash encryption (particularly the secure hash algorithm takes part of it as a key) can also be used for authentication (Figure 5).
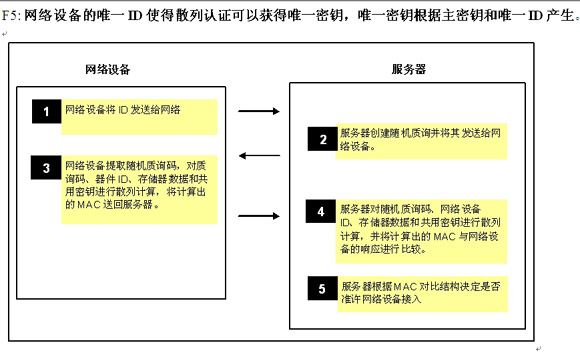
When a partial input is used as a key, the result is called an information authentication code (MAC). The hash encryption algorithm has the following characteristics: it has a high avalanche effect, and a small change in input can cause a significant output change; it must have good unidirectionality (irreversible), and the input information cannot be derived from the output data; finally It must also be able to avoid conflicts. Two different hash inputs cannot produce the same hash output. Typical hashing algorithms (shift, XOR, and) take up less system resources and have a lower implementation cost.
The premise of this solution is that the network device and the server must have a common key, which is used for MAC hash encryption calculation. If the network device has a unique identification code (ID), the ID can be used as the device's unique key.
Implementation of the hash algorithm In order to embed the encrypted hash algorithm, such as SHA-1, you can choose: microprocessor, ASIC, FPGA or vendor-specific devices (Table 1). These devices can all be used as authentication tokens for network devices to perform hash authentication. As shown in Figure 5, by performing the SHA-1 encryption hash operation embedded inside the device, the MAC is jointly generated by the network device and the server.
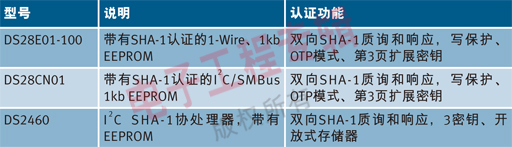
Table 1: Maxim's SHA-1 memory device
SHA-1 is a public standard defined by 180-1 and 180-2 (FIPS 180-1, FIPS 180-2) and ISO / IEC 10118-3 published by the Federal Information Commission. The SHA hash algorithm currently in use is a hash authentication method approved by FIPS. Because SHA-1 satisfies the above three principles (irreversible, anti-collision, and better avalanche effect), it has become a commonly used algorithm.
Remote upgrade function
The authentication protocol of Maxim devices provides a 32-byte authorization data page, which can be used for software management or other control. For a given hardware platform, software functions can be selected. The data on the authorization page can specify which functions are enabled. Maxim's SHA-1 memory requires a SHA-1 MAC to complete the EEPROM memory write operation. This operation also requires the server to authenticate the network device. With this function, the device can be upgraded remotely even on a network without security protection measures. When performing a write operation, the SHA-1 MAC needs to include the original memory data, new memory data, and a unique device ID.
The key of this encryption technology is to use part of the application memory data as a "random number". When writing a MAC to upgrade a function, the original function data, original random number, new function data, new random number, and unique device ID must be included. Obtain a non-repeatable and unique upgrade event calculation result and write it to a certified device. Figure 6 shows the SHA-1 MAC input of the write memory MAC, and Figure 7 shows the upgrade timing.
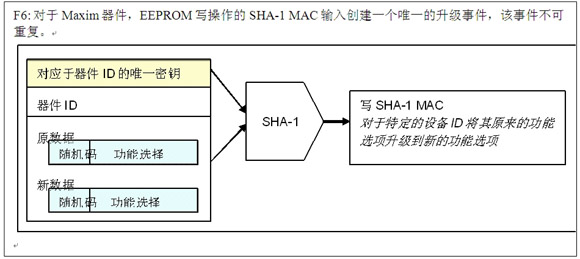
Image 6
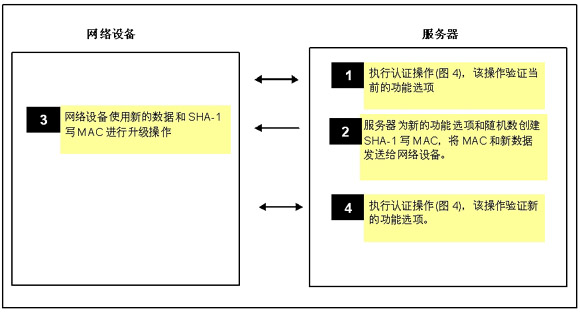
Figure 7: Perform hash authentication before and after remote upgrade to confirm that the target device is authorized and complete the upgrade process.
Applications
The working principle of the safety device based on SHA-1 in the actual system is given below (Figure 8). In the picture, the DS28CN01 authentication token is used to realize two-way authentication, and communicate with the host through the I2C interface. In this case, the main processor is the network controller, which performs data communication with the base station, and the base station communicates with the microprocessor connected to the DS28CN01. The microprocessor generates part of the random challenge code, and the host provides another part of the random code to complete the host token authentication. This technology can prevent the host from generating challenge-response pairs and confusing other systems.
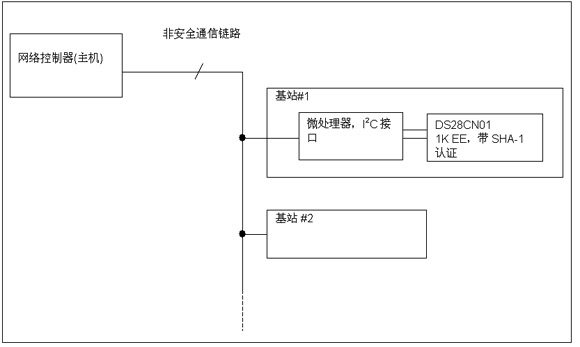
Figure 8: Two-way authentication does not require a secure network connection
The base station authentication host creates a 7-byte random challenge code and the required page number, and sends it to the microprocessor of base station # 1. The microprocessor of the base station # 1 communicates with the DS28CN01 through the I2C interface, forwards the random challenge code and calculates the page MAC on the selected page. The calculation page MAC will perform the SHA-1 operation using the page data, the unique ROM ID and the key. The base station # 1 microprocessor retrieves the MAC, page data, and unique ROM ID from the DS28CN01, and forwards them to the host through a non-secure link. The host performs the same SHA-1 calculation to verify that the MAC returned by base station # 1 is correct. If there is no match, the host will reject the network access of base station # 1.
Host authentication first executes the base station authentication process. The microprocessor of base station # 1 generates a 3-byte challenge code and sends it to the host through an unsecured communication link; the host generates a 4-byte challenge code, which corresponds to the base station's 3-byte challenge code In combination, a 7-byte challenge code is generated. This 7-byte data is subjected to SHA-1 operation together with the page data and ROM ID in base station authentication to generate a page MAC. The 4-byte challenge code generated by the MAC and the host is then sent back to the microprocessor of base station # 1.
The base station # 1 microprocessor extracts the additional 4-byte challenge code and combines it with the 3-byte challenge sent to the host to obtain a 7-byte challenge code. Using the page in the original base station authentication, the page MAC is calculated in the DS28CN01. Then, compare it with the MAC result sent by the host. If it does not match, the base station will block the host's functional options.
Fireproof safes (Fire-resistant safes) are designed to protect its contents from high temperatures and fire.
Details:
All of our products can pass CE and UL certifications;
Digital and mechanical variants available;
The effective time of resistance to damage is from 0.5-2 hours;
Door bolts are in a 4 way coverage
Financial Fireproof Safe,Lcd Display Fireproof Safe,Mechanical Safe ,Double Key Fireproof Safe
YONGFA INTELLIGENT TECHNOLOGY SECURITY CO., LTD. , http://www.yongfa-safe.com