Lei Feng network press: The author of this article is a fun hacker - security researcher, programmer, product manager; focus on information security, product operations and a variety of fun things.

The title is called "Recover old text" and talk about malicious websites because it once wrote a rather long article called "Speaking about malicious websites" and chatted about some things about malicious websites. It seems that few people or I basically don't see anyone except technology. The article writes about malicious websites, and I have been involved in this matter for some time. Therefore, I have almost forgotten what I understand, so I would like to talk to you before forgetting.
A malicious website is a more general concept. Basically, you can understand that those websites that are harmful to ordinary netizens can be called malicious websites. For example, we know that counterfeiting and fishing, such as counterfeit banks, QQ space, and other websites, are still there. Horses, gambling, and porn sites can be classified as malicious sites within a certain category.
Where do you most likely experience malicious websites? In general, we may not be very clear about what is which, what may be the most conceptual is for phishing websites, and actually most of the students should often encounter. such as:
Students using Google Chrome may often see a red warning page;
WeChat access links will also be prompted that the site is insecure and then cannot be accessed;
Security software will jump to the warning page when you visit certain webpages. An alert box will tell you not to visit this website. The website is not safe.
And ultimately, the QQ chat window gives a URL to tell you not to visit.
These may be the time when people most intuitively experience malicious websites. Why not allow you to visit these websites? This is because these websites are identified as malicious websites by the corresponding systems of these software. In order to avoid your losses, they are reminded and prohibited. You visit !
This is a relatively thin classification of my previous malicious website:
Hacking, phishing, hacking, gambling, obscene pornography, illegal trading and sales, virus Trojans, illegal activities.


I have used these two maps several times. The main thing is that people are too admired for counterfeiting. Can you tell which one is really the official website of Qiao Shizhao? Anyway, I don't know the website but only the page.
This is a typical fraudulent website. Only a little bit of seriousness can be found on the above URL (we may look a bit too abrupt, for everyone to see clearly, I use PS to deepen the next URL) to find the first map URL More than e, in addition to the same page, the URL view is almost a common way to counterfeit phishing sites, such as using 0 instead of o, such as taota0.com and taotao.com, or taobao.cm, or as in the above example Finally, add a hard-to-find letter, etc. The ultimate goal is to make the site look more like the official website. If you believe it is official website, then you will buy masks on it and the money will eventually be paid. Go to someone else's pocket and the mask will not be sent to you.
In fact, counterfeit fraud and phishing hacking are sometimes not so clear, because most of them are implemented through counterfeit pages. There are also class URLs, which may not be uncommon to everyone:
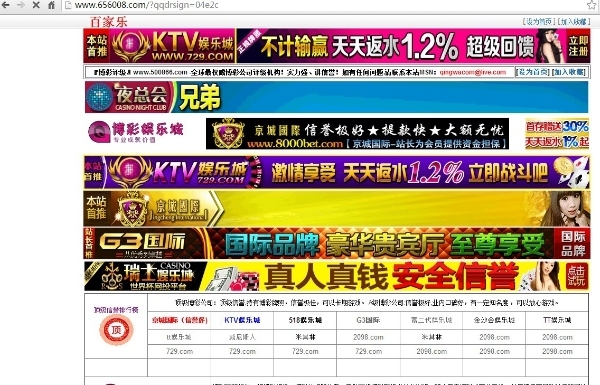
For betting on gambling, we can search through the search news of Sogou to search for the keyword “sparkling†and then click on the results of the search to experience it (If you click in and do not jump to try a few more), there is nothing to say about such sites. Don’t believe what Chow Yun-fat gambled on God’s endorsements or what’s on the list. All of them are money-making. Don’t try to try it out. Money will not come in.
Illegal violations refer more to violations of relevant laws and regulations, such as reactionary and political violations of websites, etc.; and Trojans understand that Trojans were very famous in the early days of Trojan horse monitoring. A lot of killers are being used softly, and in recent years it seems that hang-horses have basically declined; in addition, there are illegal sales and transactions that refer to websites that sell counterfeit drugs and sell various tools. Obscene eroticism is better understood. I remember that when the company was doing erotic website engine, because of the use of some algorithms, etc., training of samples was needed. So I visited hundreds of yellow websites in the office every day. It feels proud and looks like crying. Then when the engine is just doing it, there are more false positives and false negatives. It's also often manual visits to confirm whether or not pornographic websites... that kind of scenes and feelings you can understand, I won't say much. It's all tears!
In addition to counterfeit fishing, the malicious website is also hacking. The most common is really hacked, just hang a black page, write a "hacked by xx", this is no harm, most of the site is black is mainly used to do black hat SEO, for example, some engage in security The classmates may come across a shell that says that someone is looking for a news website that you have high authority to use. It is used to do similar things. In fact, these are all black production actions.
In addition to normal hacking, several common blackened forms are:
1, dark chain, also known as black chain
2, Referer cheat
3, UA cheat
Most of the dark chain will not affect the normal display of the page (the effect of the instructions get people's technology sucks ...), by adding in the page invisible labels, such as setting display: none with CSS, or setting DIV The height is 0, so that the contents of the code are not visible on the page. Then some keywords that need to be SEO are added. Generally, some high-weight websites are selected so that the search engine crawls these normal websites. You will also crawl to those additional keywords, such as adding keywords and links to some gambling sites.

The keywords at the bottom of the site are actually not visible on the page.
Followed by UA cheats, it is also a black hat SEO way. The way UA cheats is very simple. It is to judge the UA header of the website visitor. When judging that the UA is a crawler of the search engine, it returns the contents of SEO. If it is not, it returns to the normal page.

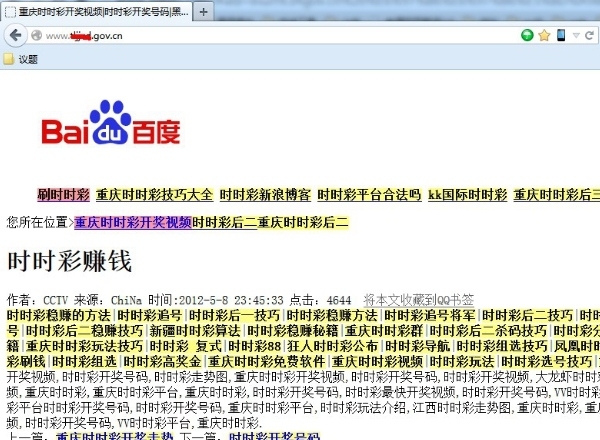
The two maps are the same URL. The former is the content displayed during normal access. The latter is the content that I modified when the browser's UA is "Googlebot/2.1" again. Because the above string is Google crawler. UA.
There are Referer cheats, or black hat SEO. Referer cheats are somewhat similar to UA cheats, but it is Referer's judgment. For example, if you click through the search engine's search results, you will see, for example, Referer with the address http://, then it will jump to the constructed address, and if you directly visit the destination URL, it will be the normal page. .
You can try using Referer for http:// to visit http:// and referer without the effect of the visit.
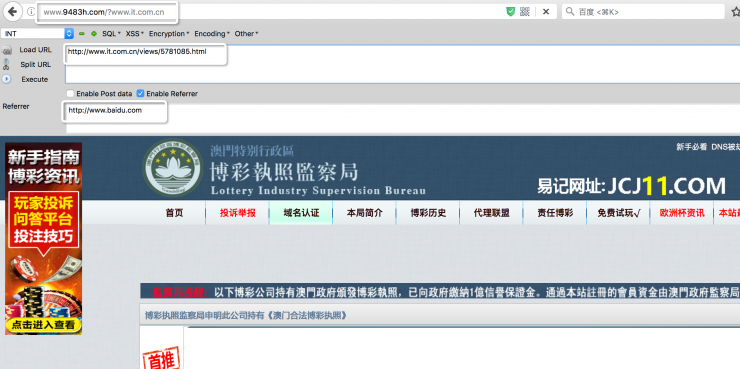

These two graphs are the visit results with Referer and without Referer respectively. The one with Referer's visit above jumps to a false website (actually a betting website). The latter is a blank page for direct access.
Probably to say this to everyone, in fact, malicious websites have many interesting points, you will find that, for example, in order to do a website full of fakes, those who do fake websites sometimes do better than they really do, and some methods include Some technical points you may not think of, including some that still use loopholes and so on. The article I wrote earlier has several examples. We are interested in taking a look at my column and I welcome you to discuss the message.
Note: The question map comes from the Internet, a network, malicious sites for some people do not understand is a network, it is difficult to break free! In fact, standing far to see, after understanding, you will find that it is easy to avoid.
Lei Feng Network (search "Lei Feng Network" public concern) Note: This article is authorized by the author to release Lei Feng network, reproduced, please contact the authorize and retain the source and author, not to delete the content.